Share this post

A social engineering technique called ClickFix has rapidly evolved into one of the most dangerous cyberattack trends of 2025. Originally identified as a deceptive browser verification scam, ClickFix has now grown into a full-fledged ecosystem, with phishing kits and malware-as-a-service tools enabling attackers of all skill levels to exploit it.
According to ESET’s Threat Report, ClickFix activity surged in the first half of 2025, becoming the second most common attack vector after phishing. The technique’s simplicity and platform independence make it especially dangerous - it works on every popular operating system.
The attack disguises itself as a routine browser security check, often resembling a fake reCAPTCHA or verification page. Victims are prompted to “prove they are human,” but behind the scenes, clicking the button copies a malicious command to the clipboard. The page then instructs the victim to open their terminal or PowerShell window, paste the command, and run it to “complete verification.”
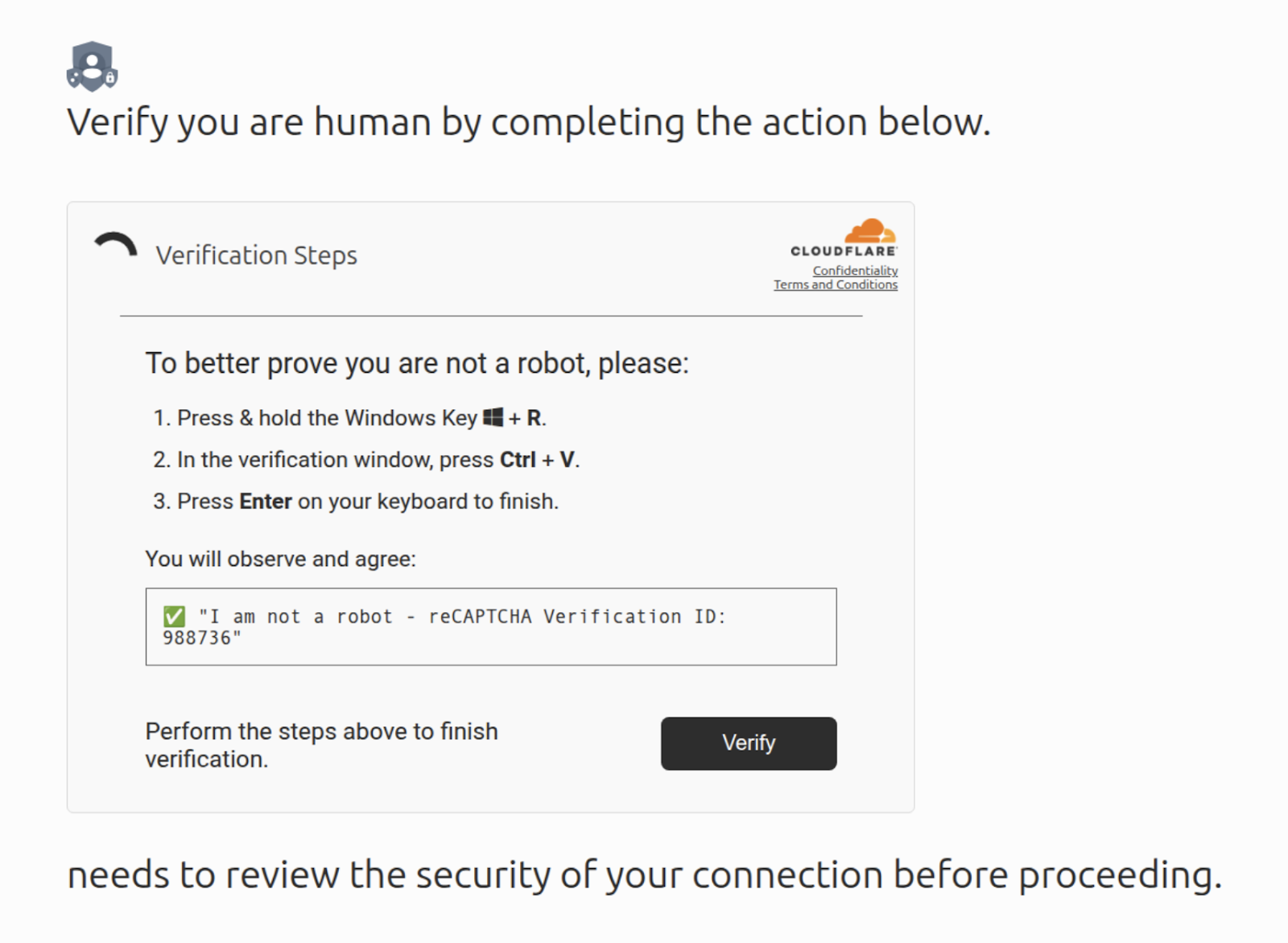
By doing this, the victim essentially becomes their own worst enemy, unintentionally launching malware on their device while believing they are making it safer. This makes ClickFix especially evasive, as the infection process bypasses automated defenses and relies entirely on manual user execution.
Researchers from Palo Alto Networks’ Unit 42 recently uncovered the IUAM ClickFix Generator, a phishing kit that automates the creation of these deceptive pages. Hosted on a server active between July and October 2025, the kit allowed attackers to fully customize their phishing campaigns, including titles, domains and malicious commands victims are tricked into running.
The tool could detect the victim’s operating system, apply JavaScript obfuscation, and even block mobile users to ensure the malicious payload executed properly on desktop environments. Unit 42 linked the kit to multiple campaigns distributing DeerStealer for Windows and Odyssey Infostealer for macOS. Both malware strains are designed to steal credentials, browser data, and cryptocurrency wallet information.
The discovery of the IUAM ClickFix Generator marks the next phase in the commoditization of phishing techniques. Much like phishing-as-a-service, this approach lowers the technical barrier for cybercriminals, enabling rapid deployment of realistic, customizable scams that trick users into infecting themselves.
Our experts warn that ClickFix’s success lies in its psychological manipulation, convincing users that they’re performing a legitimate security step when, in reality, they are launching the attack on themselves.

As this method continues to evolve, we recommend deploying our anti-phishing solution to stop ClickFix-style attacks before they reach users. Book a free demo to see how it prevents users from accidentally executing malicious commands and blocks fake verification pages.