Share this post

A sophisticated phishing campaign, tracked by Palo Alto Networks’ Unit42 since at least April 2025, uses the Browser‑in‑the‑middle (BitM) technique to harvest Meta/Facebook credentials. The campaign typically starts with a weaponized link in a phishing email (often a faux copyright or policy notice) that redirects a victim to a fake CAPTCHA page. Interacting with the CAPTCHA triggers an in‑page fake browser window, a deceptive browser interface rendered inside the legitimate browser, that impersonates Facebook pop-up login windows and displays what looks like a legitimate URL while capturing credentials. The attack still depends on social engineering, tricking the victim into clicking the malicious link and interacting with the fake page.
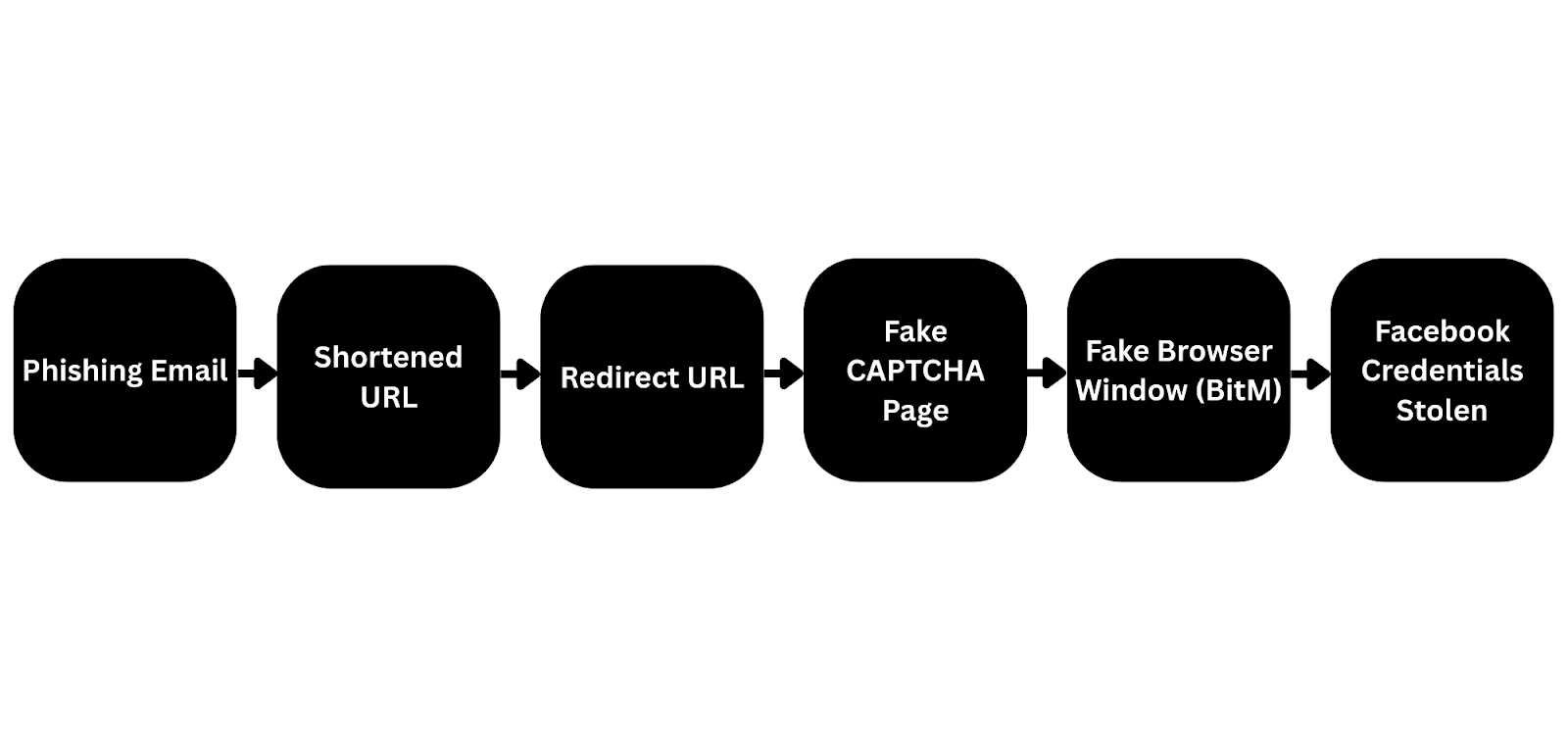
The chain begins with social engineering and a shortened link. The redirect lands the user on a bogus CAPTCHA page that, when interacted with, spawns a fake browser UI inside the real browser. The victim completes login and MFA inside that proxied browser. The attacker records the authenticated session (via cookies or by exporting the browser profile) and may then replay or resume it.
First comes emotional pressure: a copyright claim or account-suspension warning pushes people toward quick action. Impersonating a major platform (Facebook/Meta) leverages strong recognition and the expectation of legitimate, familiar login flows. A fake CAPTCHA lowers suspicion, since users are accustomed to clicking “I’m not a robot” to continue.
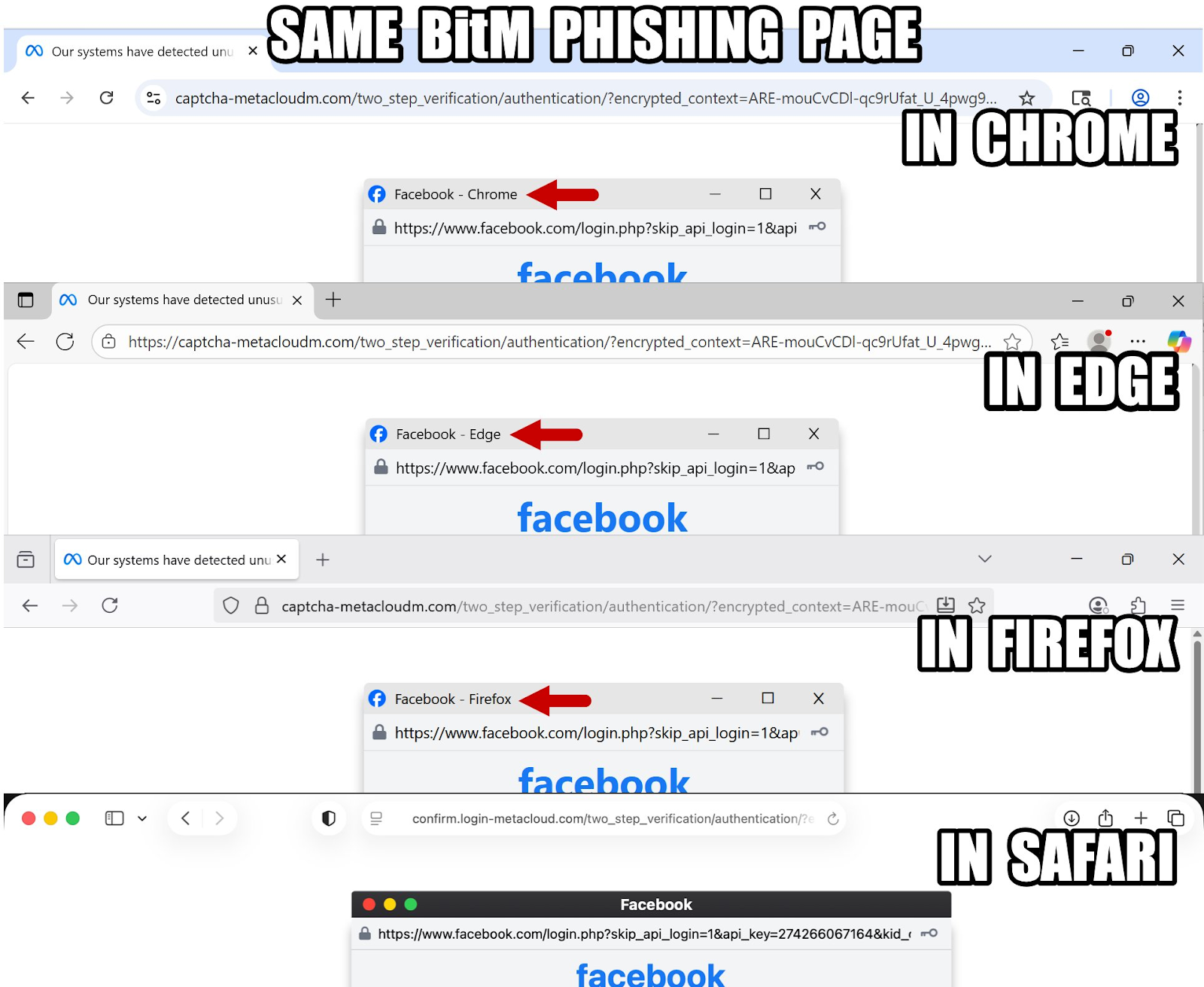
While this campaign currently focuses on Meta's ecosystem, the underlying tactics, techniques, and procedures (TTPs) are highly adaptable. They can be easily repurposed to target other platforms where account access is valuable.
This ongoing campaign showcases how Browser-in-the-Middle (BitM) phishing is evolving into a turnkey method for stealing MFA-protected sessions, leveraging social engineering, redirect chains, and fake browser environments. Compounding the threat, the campaign frequently rotates domains, making detection and blocking significantly more difficult.
The key takeaway: URL legitimacy alone is no longer sufficient to determine authenticity. Organizations must adopt layered defenses to protect against these sophisticated phishing threats.
Security awareness training by revel8 can help your company stay ahead of these evolving tactics by equipping employees with the knowledge and skills to recognize and respond to advanced phishing techniques like BitM before damage is done.