

Les attaques basées sur l’IA générative sont déjà là. Transformez vos équipes en une couche de défense proactive grâce à des simulations personnalisées, en temps réel, qui reflètent le paysage actuel des menaces.
Demander une démo

Have a live chat with the deepfake of our CEO Julius Muth!













.svg)
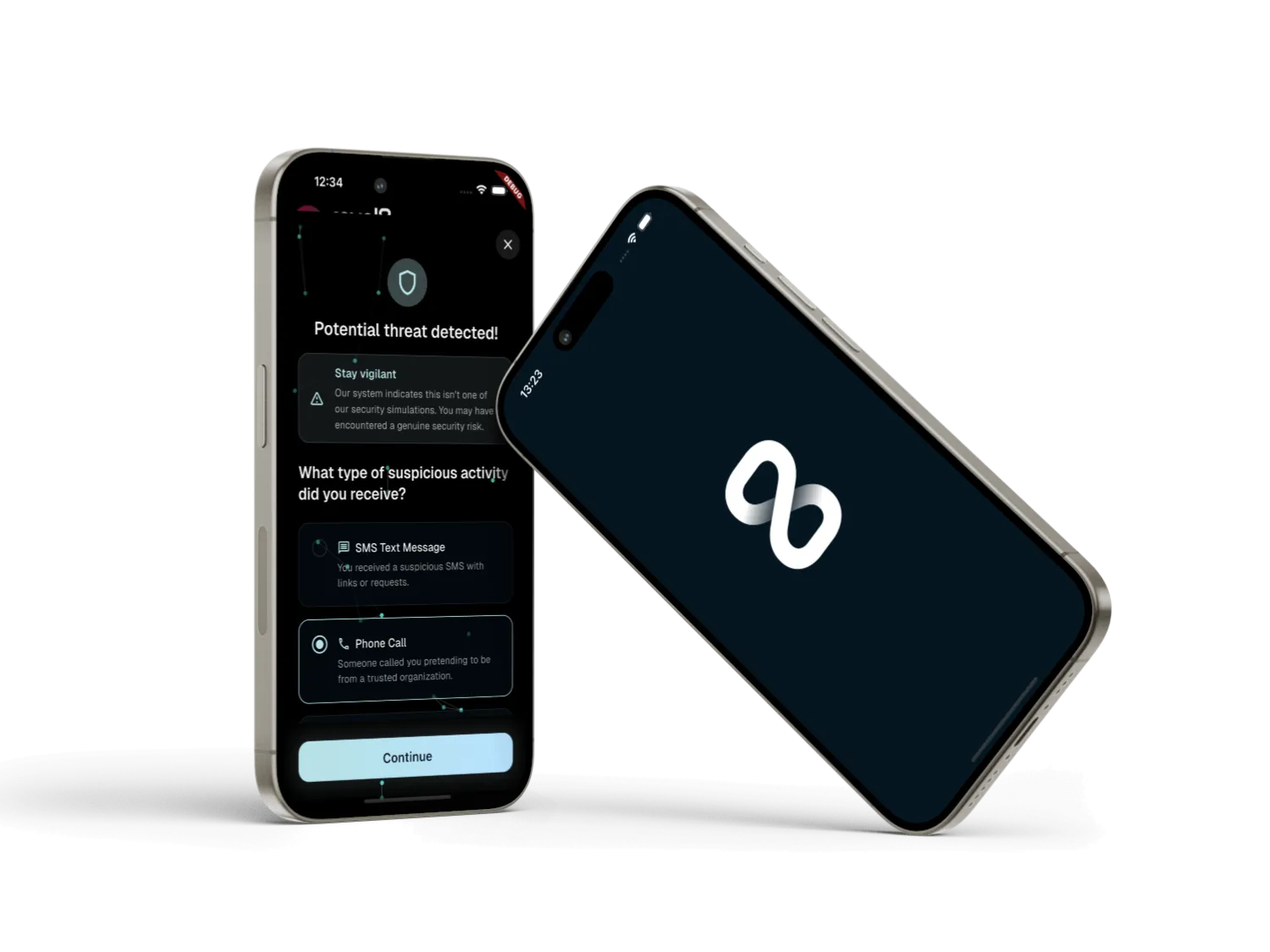

Detect, report, and react faster through real-time human signals - not delayed incident reports.
Adapt your simulation strategy on the fly. Adjust playlist speed, target specific groups, and prioritize threats. Whether hands-on or on autopilot, revel8 lets you tailor campaigns to your organization’s risk profile.
Track outcomes, surface trends, and benchmark maturity across teams. Generate audit-ready reports aligned with ISO 27001, NIS2, and internal policies. No manual tracking needed.


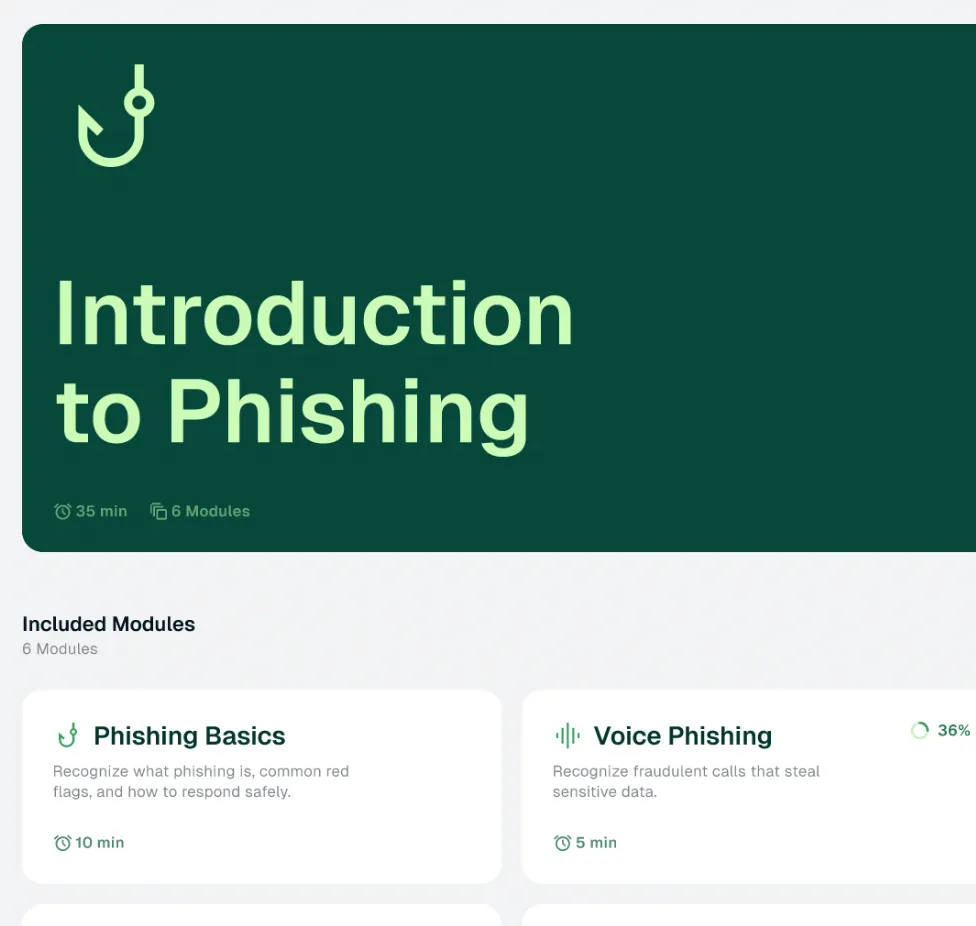
Lorem ipsum dolor sit amet consectetur molestie ullamcorp elit non diam at pharetra integer non fringilla. Non cras sapien rutrum maecenas tellus posuere faucibus tincidunt.
.webp)
.webp)
Lorem ipsum developers with enhanced code management host private lorem ipsum repositories.
Lorem ipsum platform makes email marketing accessible for busines and design beautiful campaigns.
Aether prioritizes privacy and security and end-to-end encryption ensures your messages.
Zenith the email overload! Slack streamlines communication for teams, fostering real-time conversations.
Back up your essential documents
and files with Google's industry-leading security infrastructure.
Chronos connects them seamlessly automate repetitive tasks, streamline processes, and free up your time.
Nexsuo empowers designers with intuitive tools for prototyping, collaboration and craft stunning interfaces.
Harries brings your community together voice chat, text channels, and custom roles create a thriving online hub.
Opera seamlessly combines notes, tasks, wikis, databases, and organize projects and more in one platform.