Share this post

In the constantly evolving landscape of cybercrime, threat actors are quick to adapt and exploit platforms that offer speed, anonymity, and broad reach. While email and SMS remain staples, instant messaging platforms have increasingly become fertile ground for malicious activities. Over the past few years, Telegram, known for its encrypted messaging and channel functionality, has seen a significant surge in its use by phishers and scammers, fundamentally altering how these fraudulent operations are organized and executed.
Telegram's core features - end-to-end encryption, secret chats, large-scale channels, and anonymous bot functionality - were designed to prioritize user privacy and communication freedom. Ironically, these same features provide an ideal operational environment for threat actors.
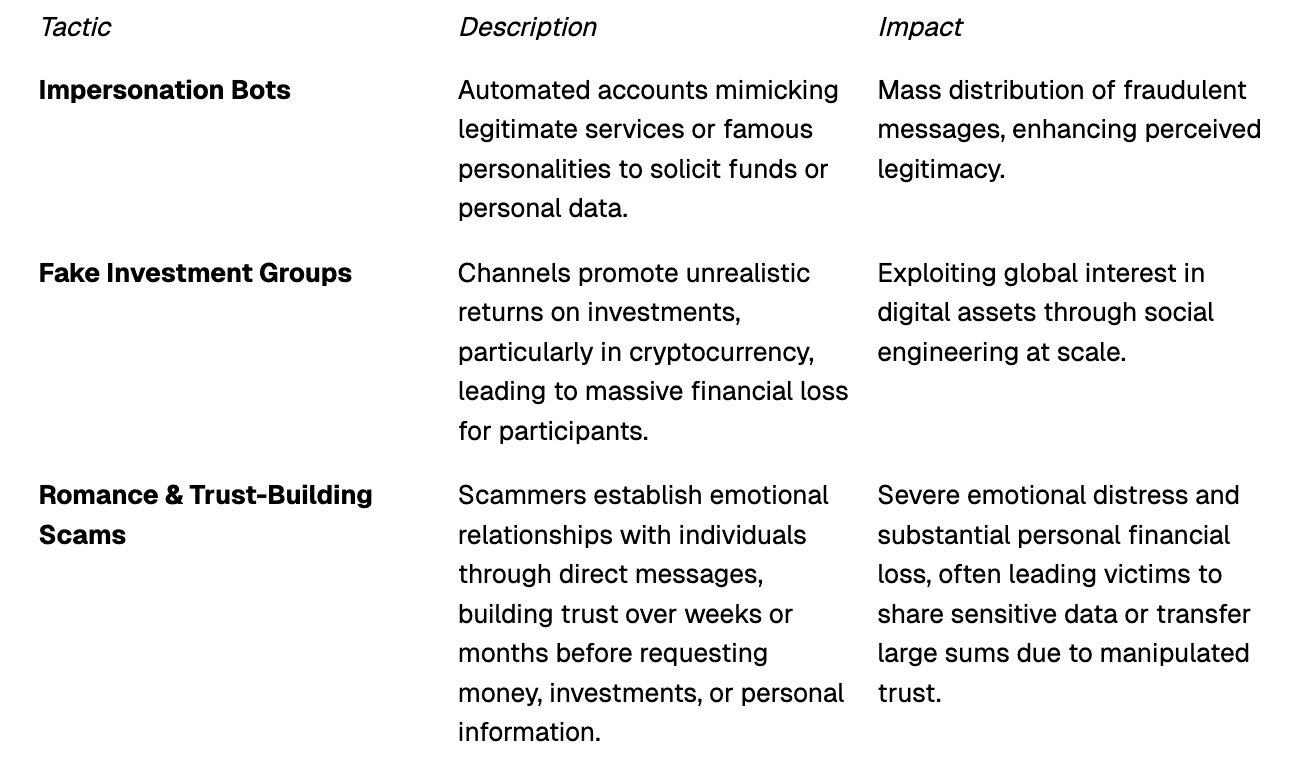
Telegram is now being leveraged across the entire spectrum of phishing and scam campaigns:
Large, private Telegram channels and groups serve as marketplaces and communication hubs for cybercriminals. Here, actors buy, sell, and trade stolen credentials, phishing kits, exploit tools, and access to compromised systems. This infrastructure allows for rapid communication and coordination among distributed criminal groups, making it difficult for law enforcement to monitor or dismantle these operations.
The platform is a major incubator for Phishing-as-a-Service (PhaaS) offerings. Scammers can easily purchase full-service kits, including pre-built phishing pages, automated message bots, and scripts designed to harvest credentials from victims. This dramatically lowers the barrier to entry for novice criminals.
Beyond merely organizing scams, Telegram is increasingly used as the direct delivery vehicle. Scammers utilize the platform to:
A concrete example is the “Booking.com side job” scam that spreads via Telegram. You’re contacted out of nowhere with an offer to do simple remote tasks for a “hotel booking platform” like optimising reservations or reviews. The pay sounds great for just an hour of work a day, and you’re quickly moved into a group chat with a “mentor” and fake participants posting screenshots of big daily earnings.
To start, you’re told to register on a professional-looking site that uses Booking-style branding and then “recharge” your account, usually via crypto, so it has a positive balance. After a few dummy “booking tasks”, your dashboard shows rising commissions and often even allows a small withdrawal, which convinces many people it’s legit.
Once you’re hooked, the trap closes. Suddenly, your account shows a negative balance or “locked” commissions. Support insists you must deposit more to fix it, unlock profits, pay fees or taxes, and each payment only unlocks a new invented condition. In the end, there is no job, no partnership with Booking.com. Just a fake platform designed to keep you paying into it until you give up.
While Telegram's security features are robust for legitimate users, the environment necessitates vigilance. Organizations and individuals must implement layered defenses:
The shift of malicious activity onto Telegram highlights a critical challenge: as communication technology advances, so too do the methods of those seeking to exploit it. The platform's utility for privacy makes it a double-edged sword that will likely remain central to cybercrime operations for the foreseeable future.
With scams moving beyond email to messenger apps, voice calls, and deepfake lures, organisations need security awareness that mirrors real threats. revel8 addresses this by creating dynamic, evolving training grounded in attacker behaviour. Human risk isn’t static: exposure depends on role, public footprint, and recent behaviours. revel8 personalises simulations using OSINT and real threat data, keeping exercises contextual and realistic.
Simulations now extend beyond email: voice phishing, SMS, social media lures, and AI‑generated deepfakes are included. revel8 also now supports Telegram for simulated phishing, letting organisations safely test reactions to messenger‑based scams like fraudulent job offers or credential‑theft attempts. Learning is adaptive: mistakes trigger immediate, contextual feedback or micro‑training. Threat reports from staff feed back into the system to improve simulations and real-world defences.
With scams spreading across channels like Telegram, WhatsApp, SMS, or cloned‑voice calls, organisations need continuous, realistic training. Including Telegram ensures employees are prepared wherever attackers strike, keeping the human firewall robust against modern social‑engineering threats.